

Have a great weekend folks 🎈.
Despite the numerous benefits brought by technological growth, the rise of cyber crimes has become a threat in our day-to-day lives. While watching some of the hacking scenes in movies ,an unknown fear arises. It creates a dilemma regarding whether we are living in a secure society or not.
In this blog, we will analyze cyber attacks as depicted in Tamil movies.
The attacker can eavesdrop the communication, modify the exchanged data , or inject any malicious content into the communication stream.
It is a kind of a Man-in-the-Middle (MitM) attack. It takes place when an attacker sets up a fake Wi-Fi access point and forged the users to connect with this instead of a trusted network.
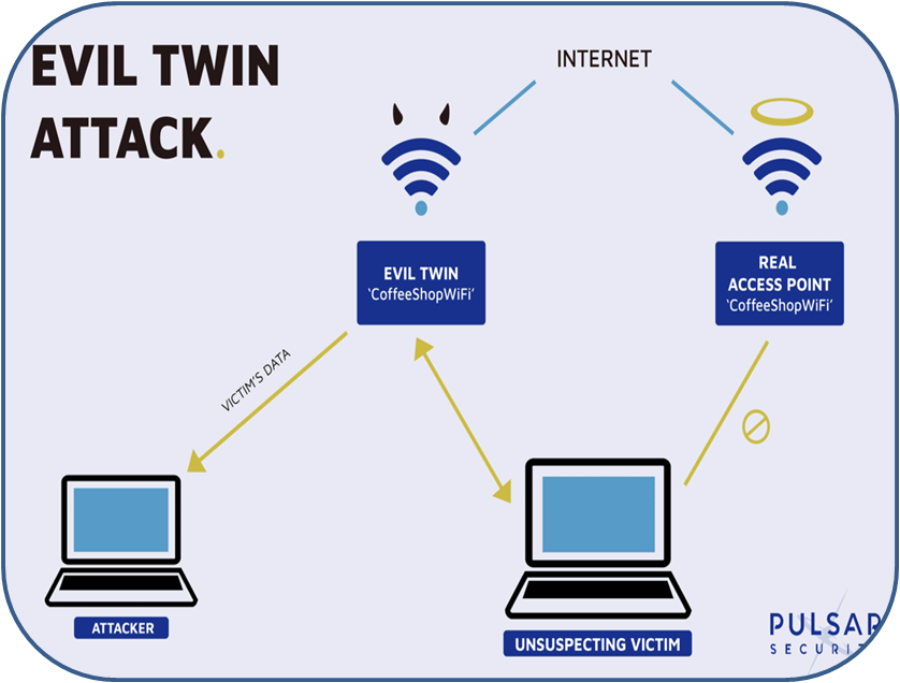
An attacker can create an evil twin with a smartphone or other internet-capable device and readily available software. These attackers mainly target the public Wi-Fi networks.
Have you ever watched the Singam 3 movie?
If yes then tell me, What do you think while watching this scene?

In this movie, after an unknown threat from the villain (Vital Prasad), Durai Singam (hero of the movie played by the actor Suriya) went to Australia to find the person who was behind this.
After reaching Vital's office, Durai Singam asked for a public Wi-Fi password to one of the receptionists. He made a call to Murali (hacker in this movie) who was in Chennai. Murali instructed him to plugin a device in his laptop.
Then a screen like this will be displayed.
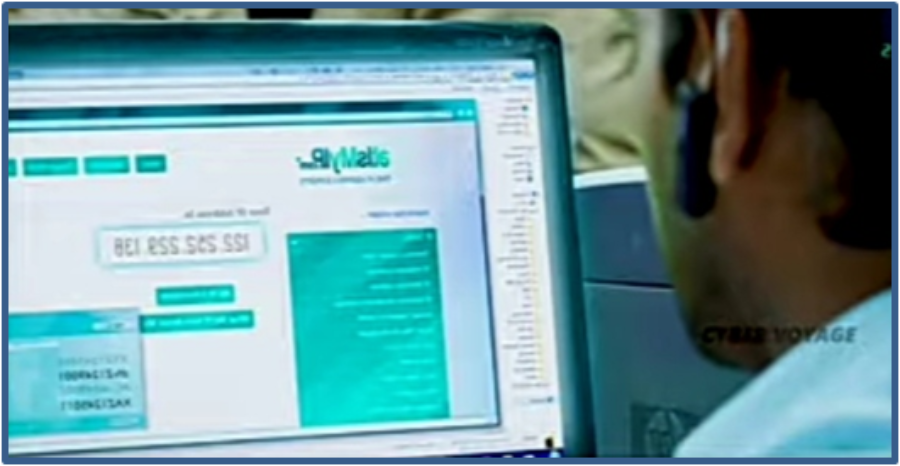
Murali asked him to enter the password details. Following that, the transmission of data was completed.
Actually what happened in this scene? How did the attacker steal the data?
The attacker creates a fake Wi-Fi access point similar to the open Wi-fi. When the users connect to this access point, all data they share with the network passes through a server controlled by the attacker. Those transmitted packets are captured by the attacker who decodes them to steal their data .
For an example if an internal employee connects to this network, whatever he is doing in online like browsing details, login credentials etc.. is visible to the hacker .
In this way the attacker stole all the data.
Thanks for reading😇. I hope this blog help to get a clarity on this scene and Be cautious while using the public Wi-Fi networks 🤫.
P.s: Comment down, if you like to analyze the portrayal of cyber attacks on another movie 😋.






