

In today's digital work, protecting our work and copyright is important. Watermarking and steganography are the techniques in which the digital image is modified in a manner that one can see the background image or the text irrespective of corruption in the image. Both techniques are used for information hiding.
Watermarking: Watermarking for centuries has commonly been used in money and stamps, and goods detection to help identify counterfeiting. In watermarking, data hidden is known as a watermark, it detects the owner of the multimedia. Watermarks are better for promoting brands.
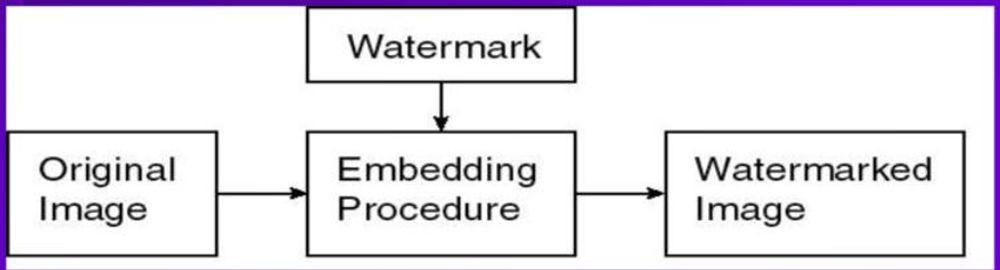
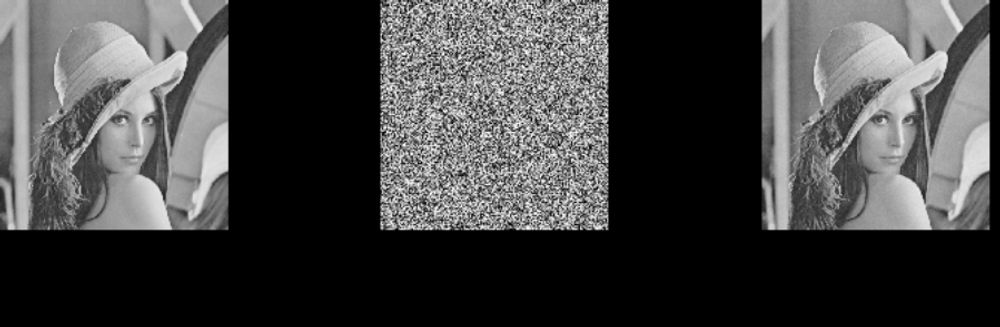
Digital Watermarking: The digital watermark is a type of digital signal or pattern which is inserted into a digital image. It can be audio, video, or image which allows us to know the owner or authority of the copyright. Watermarking is used mainly for copyright protection, source tracing, and annotation of photographs type of applications.

There are mainly two types of digital watermarking that are:
The word ‘Steganography’ is derived from the Greek words ‘steganos’ which means covered or secret and 'graphy' which means writing or drawing. It is the process of hiding secret data within a common, non-secret, file or message to prohibit detection. Some of the common techniques used in steganography are the least significant bit, palette-based technique, secure cover selection, etc.
There are softwares readily available for performing steganography. Steganography messages might be encrypted or non-encrypted, this technique is used in industries as well. The main purpose of steganography is information and communication security.
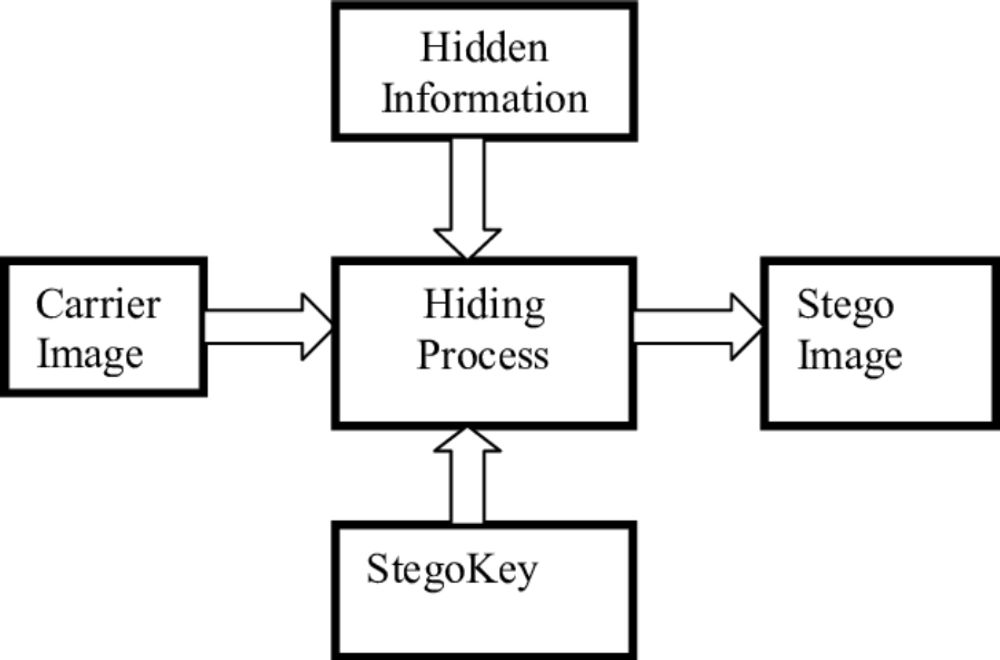
There are different types of Steganography that are as follows:
Steganography and watermarking also hide the mere presence of the message in the communicating information. Both are insecure if their detection is possible. In steganography, communication is generally a point-to-point type(between the sender and the receiver), while the watermarking techniques are a one-to-many communication type. Both techniques are easily suitable, and effective to start with. Depending upon the type of applications these techniques are used.
Hope you like my blog. Kindly read, like, and comment on my blog. Keep supporting and following. Thanks for reading my blog!!!








